- Understanding Cloud Data Protection
- Challenges of Data Protection in Cloud Environments
- Visibility of Data
- Accessibility
- Controls
- Inconsistencies
- Compliance
- Analyze the built-in security
- Keep inventory of your data
- Understand your shared responsibility model
- Pair authentication with encryption
- Set up a strong credentials policy
- Use security-enhancing tools
- Identify security gaps in systems
- Establish a zero-trust framework
- Consistently back up your data
- What role can Appinventiv play in protecting enterprise data in cloud environments?
- FAQs
Data is an invaluable asset for both enterprises and their clients. Easily accessible and properly secured data combined with insightful analytics promotes corporate innovation, boosts customer satisfaction and loyalty, and most importantly, gives you a competitive advantage in the marketplace. Nowadays, businesses continually replace outdated, on-premises file storage systems with more recent, cloud-based alternatives. The introduction of the cloud has sped up IT modernization because of:
- Easier scalability
- Lower expenses
- The capacity to modify IT architectures in response to changing business needs
But the news isn’t all good. Traditional security mechanisms, which were created to protect data and programs running on on-premises systems, have been undermined by the adoption of the cloud. Now, protecting your cloud-based data is a very different matter.
![]()
The increase in cloud computing and cloud-based storage has created a plethora of chances for cyber criminals and other undesirable individuals to try to access and damage your data.
![]()
66% of IT experts believe that security is a top concern when using enterprise cloud-based computing platforms. These worries include the potential for malevolent actors from within the corporate structure, account takeovers, and significant data breaches.
According to IBM and the Ponemon Institute’s Cost of Data Breach Report of 2021, the average global cost of a data breach reached $4.24 million in the year 2021. This was an increase of 10% from the previous year. It is thought to be brought on by higher regulatory fines and the effects of remote work during the COVID-19 pandemic.
So what should companies do to protect cloud data? Many things, most of which are straightforward safety precautions.
The majority of cloud service providers follow the “shared responsibility” principle, which states that security is the responsibility of both the vendor and the client. While the cloud platform will guarantee the security of the cloud infrastructure, the enterprise is responsible for ensuring security on its end by safeguarding its data and login credentials against security threats and limiting access to that data.
Below, we will learn what cloud-based data protection is, its challenges, and the best practices enterprises can follow to protect data in a cloud environment.
Understanding Cloud Data Protection
A specific model of data security known as “cloud data protection” is used in order to safeguard data stored in a cloud environment, irrespective of whether the data is at rest or in motion. With enterprise cloud data protection, data is secured and protected on the cloud against loss, theft, or abuse due to unauthorized access, breaches, and infiltration.
To provide the highest level of security, a cloud data privacy and protection plan must be developed to guard all types of data, including:
- Data in Use: This is crucial information that is being used by a program or application currently via user authentication and access control.
- Data in Transit: This is private data traveling over a network through encryption or other protection controls.
- Data at Rest: This refers to the information that is presently being kept on-site or in the cloud.
In general, enterprise cloud data protection and privacy will secure your data by defending consumer and company information from both external and internal attacks, as well as protecting data by backing up and restoring processes and systems. Additionally, it entails preserving data privacy by creating control access for specific segments, which guarantees that only a few authorized people have access to important and sensitive data.
Challenges of Data Protection in Cloud Environments
Numerous security challenges are brought on by the complexity of cloud architectures, along with the increasingly strict data protection and privacy laws and vendor shared responsibility models. Enterprises may face the following major difficulties or challenges:
Visibility of Data
Keeping an accurate inventory of all applications and data, which is very important for data protection, can be challenging for enterprises.
Accessibility
Compared to on-premises infrastructure, there is less control over data and applications hosted on third-party infrastructure. It is not always feasible to see what other users are doing and discover how devices or data are being used.
Controls
Cloud vendors provide a well-known “shared responsibility model”. This indicates that while cloud users have more control over some security features, others are still under the vendor’s control, and users cannot guarantee security.
Inconsistencies
Since different cloud providers offer a range of capabilities, cloud data privacy and protection may vary.
Threat actors may take advantage of these issues to cause security lapses, the loss or theft of trade secrets and private or financial information, malware infections, or ransomware infections.
Compliance
It is another significant factor. Enterprises are expected to abide by data protection and privacy rules and regulations, such as the Health Insurance Portability and Accountability Act (HIPAA), 1996, and the General Data Protection Regulation (GDPR) of the European Union. Setting uniform security standards across cloud environments and demonstrating auditor compliance may be quite challenging for businesses. This could be the reason the market for data protection is anticipated to reach $158 billion before 2024.
Cloud Data Security Best Practices
Cloud computing has undoubtedly given enterprises access to storage and processing capacity in a flexible and scalable fashion, but as we mentioned earlier, security is still a major concern.
According to Gartner, in 2020, preserved personal data represented the main area of privacy and security risk for 70% of enterprises. Organizations that were found to be weak in privacy protection by 2021 incurred heavy compliance expenses that were more than twice as high as those of their prepared competitors.
So it’s crucial to set security best practices that work for your company because cloud providers might not be as accountable for the security of your data as you might believe.
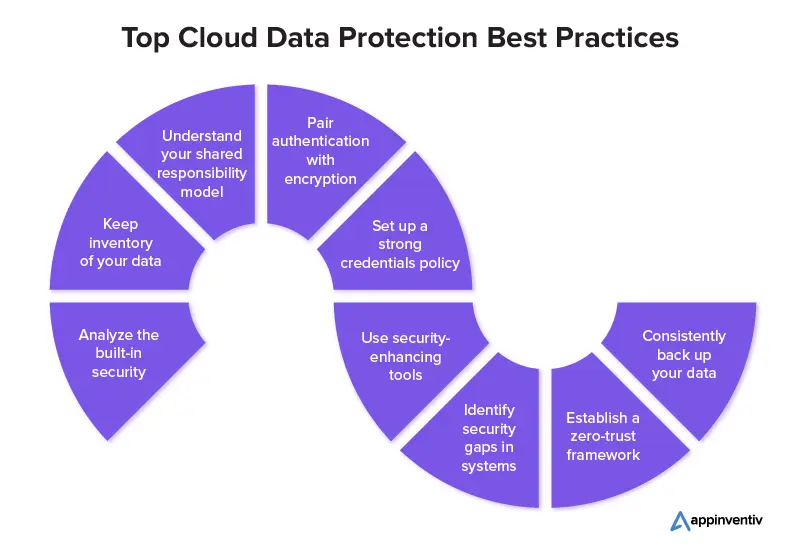
The following is a list of cloud data security best practices that an enterprise can follow.
Analyze the built-in security
Any cloud provider you select should be well-equipped with reliable tools to protect enterprise cloud data security and strong internal controls. In order to ensure that systems are properly safeguarded, look for providers who offer service-level agreements. Additionally, they ought to be open and honest with their clients about their compliance standards. Verify the policies that vendors have, to ensure compliance with regulations as well. These vendors should also be certified to meet compliance requirements and offer your organization transparent services.
Keep inventory of your data
It is far more challenging to accurately evaluate any potential hazards without a complete list of your assets. The identification of the appropriate controls required to safeguard sensitive data may become even more challenging as a result.
Therefore, you should first determine the kind of sensitive data you have to secure and protect in order to create the optimal cloud data security and protection strategy. Consequently, you must determine the kind of data that requires protection and its location.
You can create a strong program for cloud data security and protection as well as strengthen accountability for all employees inside the company and boost productivity. It can further enhance the procedures for reporting, making decisions, and performance optimization.
If you are looking to implement a DLP strategy for your business, our extensive guide on data loss prevention and its best practices will guide you to the best approach.
Understand your shared responsibility model
In a private data center, security is solely the organization’s responsibility. However, the boundaries can become a little hazy in a public cloud. Popular IaaS and PaaS providers like AWS and Azure provide documentation that precisely outlines who is in charge of each component, so make sure to read and comprehend this.
![]()
Pair authentication with encryption
The protection of data and other cloud assets can be improved significantly through authentication. However, there will always be a chance that hackers will pretend to be authorized users to access private information. Therefore, encryption is crucial as well.
Encryption scrambles the data using encryption keys (randomly created passwords) as an additional degree of security. You should also think about file-level encryption. Adding another layer of security to data before transferring it to the cloud can act as the basis for your cloud security and protection.
Additionally, data can be divided into small pieces or shards such that each piece is saved separately. This reduces the risk of a complete file being easily compiled if someone breaches the system. This type of cloud security risk management strategy needs to be implemented for ensuring end-to-end protection.
Set up a strong credentials policy
Ensuring that there are both rigorous access rights and strong credential policies is another way to improve cloud data breach protection. Data breaches and assaults can be avoided by using strong credentials. Access control is one of the best types of cloud data protection. And thanks to strict permissions, only the data that individuals and programs need can be accessed by them.
Robust credential policies should be implemented in order to stop attackers from exploiting the permissions granted to these users and programs. You should routinely examine your passwords and permissions. Check to see if each credential in the system is truly being used. You should also check whether people are using the same passwords frequently and if passwords are difficult enough to guess.
Use security-enhancing tools
You can use a few third-party apps or tools to further safeguard your data:
- Cloud storage entry points: The entry points enable the transfer of data between local hot storage and cloud cold storage. A good entry point can lessen bandwidth issues, security hazards, and latency. It will ensure that edge-generated data is retained, access is permitted across data tiers, and security is upheld.
- CSPM: A group of security technologies known as Cloud Security Posture Management helps find and fix potential security problems, thus decreasing attack opportunities. The procedures are automated and continuously scan cloud systems for vulnerabilities. If anything is found, they will notify the customer.
- SIEM: The Security Incident Event Management tool uses analytics and artificial intelligence to identify internal and external actions that could lead to threats. SIEM continuously updates its threat awareness and can effectively respond to security events as they occur.
Identify security gaps in systems
Usually, cloud environments are interconnected with other services and systems, some of which are internal and others external. Gaps increase when you add more vendors and systems to the stack. The security of the information and resources shared and used by these systems must be ensured by organizations by identifying each security gap and taking the necessary precautions.
Organizations are supposed to set up their own procedures in order to maintain compliance and security, even while some are implemented by outside vendors. Specific security procedures must be followed by every sector of business, as third-party vendors do not always offer the same level of compliance.
Looking to migrate your assets to the cloud? Check out our latest blog on Cloud Data Migration – Adopting the Right Strategy and Best Practices to understand the process in detail.
Establish a zero-trust framework
Enterprises should search for solutions that aid in the establishment of a zero-trust framework in order to develop complete, all-encompassing enterprise cloud data protection and privacy solutions. Zero trust uses context—including device, user, content, and application—to build trust before a link is formed, which helps an enterprise handle the specific cloud security concerns your organization is facing.
Zero trust enables you to proactively defend access to your assets, giving you the edge over data-hungry cyber threats as your business uses cloud services to boost flexibility.
Consistently back up your data
Replicas of data must be made and kept apart from the main repository at regular intervals. Regular backups aid in defending the enterprise from important data losses brought on by a lockdown or data wipeout. Data replicas also allow for ongoing offline work whenever cloud resources are unavailable.
What role can Appinventiv play in protecting enterprise data in cloud environments?
Cloud data security and protection need to be taken more seriously as more and more businesses move their data to the cloud. Remember that any successful cloud data security and protection strategy is tailored to your organization while keeping scalability in mind. The advantages of such an approach simply cannot be disregarded.
For this reason, having a dependable business partner who is highly knowledgeable about privacy, security, and cloud deployments is essential. Appinventiv offers an unrivaled depth and breadth of expertise in managed cloud services, with almost a decade of experience in the sector. With experience working with top cloud providers like Amazon AWS, Microsoft Azure, and Google Cloud, we are exactly what you’re looking for in a cloud consulting firm.. With experience working with top cloud providers like Amazon AWS, Microsoft Azure, and Google Cloud, we are exactly what you’re looking for in a cloud consulting firm.
For IKEA, the largest furniture retailer, we created an ERP solution on the cloud that became the biggest source of ROI, as claimed by the client. Similarly, by providing a cloud-based job search platform, the entire recruitment solution was brought on a mobile app of JobGet, which in turn, helped them raise a funding of $ 2.1 million.
Our successful cloud-based IoT driver assistant application created for ActiDrive, provides a complete touch-free solution to the drivers enhancing their safety and security while driving. A whopping 50K downloads is a testament to our innovation and expertise in the sector.
With our cloud consulting services, you will receive the best benefits of cloud computing in terms of efficient delivery, lower costs, dependability, high security, and top-notch performance.
FAQs
Q. How secure are cloud services?
A. The level and quality of service determine how secure a cloud solution is. For instance, due to the rigorous security standards adopted by the banking industry, people believe that online banking is safe. Similarly, for many reasons, cloud solutions are more secure than traditional on-premise ones. Using a cloud provider guarantees that the servers hosting the data for your enterprise are often updated with the newest security measures, perform auto-patching, and possess built-in firewalls.
Q. What security aspects set a private cloud apart from a public one?
A. A public cloud is used by many people, but a private cloud is solely for you. The delivery can typically be customized in a private cloud, whereas in a public cloud, it is generally “one size fits all.” When it comes to security, public clouds are equally as secure as private clouds. Unlike conventional IT, which hosts data and programs within a self-controlled infrastructure, cloud computing services offered by public cloud vendors host applications and data with a third party.
Q. What are the types of cloud data protection?
A. Data protection techniques applicable to cloud computing include authentication and identification, access control, encryption, secured deletion, verification, and data masking.



Cloud Manufacturing Software - Benefits, Types, Development Process and Cost Analysis
Cloud computing is set to become a bigger part of the manufacturing industry's future as it continues to embrace digital transformation. With advancements in manufacturing software, cloud-based solutions are here to stay and only grow with time. The potential of ERP can be realized with the help of cloud manufacturing software, which eliminates the need…

Cloud Computing in Oil and Gas Industry - Identifying Business Opportunities and Challenges
In an industry where the pressure of data is as intense as the pressure in the deep sea, oil and gas companies grapple with managing enormous volumes of information, streamlining operations, and controlling costs. Traditional systems often buckle under the weight of this data deluge, leading to fragmented processes, operational inefficiencies, and hefty capital expenditures…