- Understanding the challenges of cloud application security
- Top cybersecurity risks to watch out for in 2023 and how to address them
- Moving beyond VPNs
- Network-connected devices
- SaaS security concerns
- Endpoint-to-cloud security
- The benefits of a comprehensive cloud application security solution
- The obvious protection from cyber attacks
- Compliance with Data Protection Regulations
- Improved app performance and scalability
- Better Visibility and Control
- Cost saving
- Improved collaboration and data sharing
- Essential components and best practices for a robust cloud application security solution
- The importance of DevSecOps in mobile app security in the Cloud
- Compliances and standards of cloud application security
- How can Appinventiv make your cloud application secure?
- Frequently Asked Questions Aout Cloud Application Security
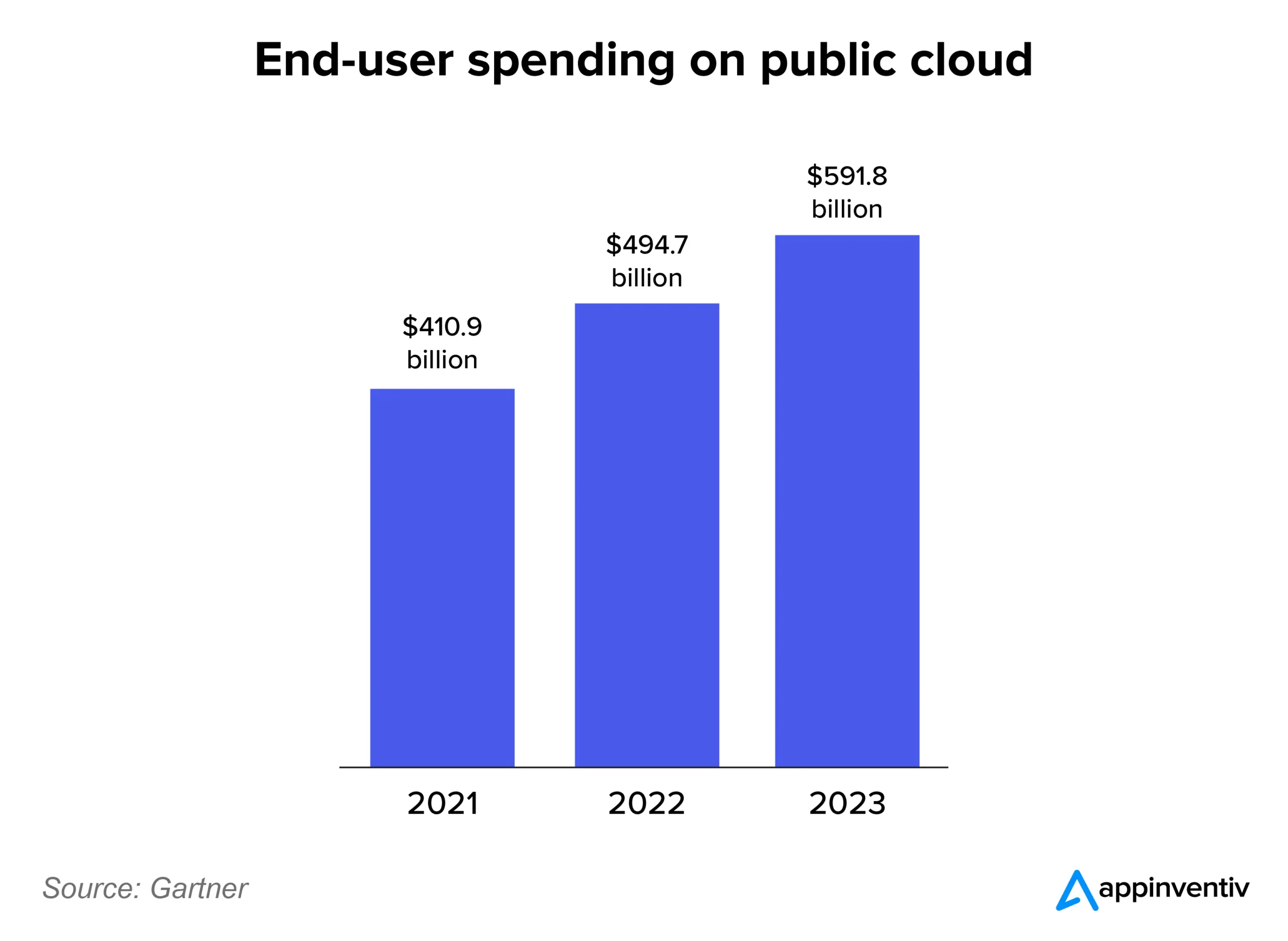
COVID-19 Pandemic brought a multitude of changes to how we live and work. One of the most influential acceleration businesses underwent was moving to cloud computing. Moving way past being a buzzword or trend, transitioning to the cloud is a necessity now that every business, big or small, is realizing. That is why end-user spending on the public cloud market has been ballooning rapidly, increasing the need to address cloud application security.
With a growth rate of 20.7%, the spending is expected to reach a total of $591.8 billion in 2023, according to Gartner forecasts. Compared with 2022, the growth has marginally paced up, with the growth in 2022 being at 20.4% and reaching a value of $494.7 billion (which was $410.9 billion in 2021). But, something that Spiderman didn’t mention, with so much data comes much greater risk.
Cloud-based application security is something that every business and cloud consulting services provider is prioritizing. All the more so because cloud applications infrastructure services (PaaS) and cloud application services (SaaS) will witness a growth of 23.2% and 16.8%, respectively.
With so much growth and so much data, it is unavoidable that cyber threats of unimaginable magnitude will keep cropping up. Whether the Home Depot data breach of 2014 or the Linkedin breach of 2019, one thing that has become evident is that cybersecurity is becoming a business priority now. Especially now that the global economy is inching towards a recession, cybersecurity will take even more prominence as cyber attacks skyrocket during recessionary periods.
Sachin Gupta, Panos Moutafis, and Matthew J. Schneider also opined a similar sentiment in a Harvard Business Review article, mentioning that “as companies collect more data — and rely more heavily on its insights — the potential for data to be compromised will likely only grow.” The HBR article goes on to suggest that to protect the consumer’s data, companies should use edge computing to limit the touchpoints consumer data has to go through, in effect limiting the likelihood of breaches.
With cloud app security measures taking center stage, adopting and deploying cloud security solutions is a crucial undertaking for any CTO out there. HBR is suggestive of limiting the data that reaches the public cloud. However, there are several other ways for you to protect the data of your company and your consumers. By adopting cloud application security best practices and implementing strategic security initiatives, companies can build resilience, prepare for the worst-case scenario and have a roadmap for thwarting cyber attacks in the nick of time.
However, before getting into the details of securing cloud applications, let us first understand the various security issues.
Understanding the challenges of cloud application security
Even in 2023, securing cloud applications is something that not every organization does perfectly. Hence the breaches. Some inherent challenges and roadblocks leave companies and their data vulnerable to cyber threats. Here are some of those challenges:
- Identifying potential risks: The process of ensuring a threat-free cloud architecture begins with identifying the potential risks associated with cloud application security. Understanding the current cybersecurity landscape and anticipating different threats can help organizations better prepare and limit their exposure to such incidents. Internal and external threats should be carefully analyzed to determine vulnerabilities in Cloud app data protection
- Evaluating the impact of security incidents: Organizations often find it challenging to assess the damage and the impact of security breaches. Loss of revenue is just one aspect of this impact. Loss of reputation, legal complications, and loss of customer trust are some of the hidden costs of neglecting cloud application security architecture.
Since some of the losses are not quantitative in nature, it becomes difficult to put the finger on the actual loss to the business. Evaluating the impact accurately can help businesses prepare a contingency plan while identifying key stakeholders and preparing an incident response plan.
- Pre-planning an incident response: While discussing securing cloud applications, it essentially circles around pre-planning an incident response. A well-defined incident response plan can help organizations save millions in lost revenue and trust.
But pre-planning an incident response is easier said than done. From detecting to thwarting, the plan should be well defined, having step-by-step details of the action plan that needs to be followed in case of a breach.
- Lack of compliance and IT expertise: Another challenge that plagues organizations is the lack of compliance towards security standards and lack of cybersecurity expertise. Privacy regulations include the General Data Protection Regulation (more on compliances below).
Without the necessary compliance and expertise, companies face a perpetual threat of becoming a victim of cyber attacks. Without appropriately securing cloud applications either by non-compliance or while not being technically sound, companies face a larger threat of a massive data breach the likes of which we may not have seen till now.
- Shared responsibility of cloud provider and business owner: Another challenge that becomes a bottleneck to having secure applications in the cloud is a lack of understanding towards shared responsibility. Application security in the cloud is ensured by both the cloud service providers (CSPs) and business owners.
However, a lack of understanding of the roles of each, CSPs being responsible for securing the underlying infrastructure and businesses responsible for securing their data and applications, can expose the business to various cyber threats.
You might also be interested in reading our definitive cloud computing guide
Top cybersecurity risks to watch out for in 2023 and how to address them
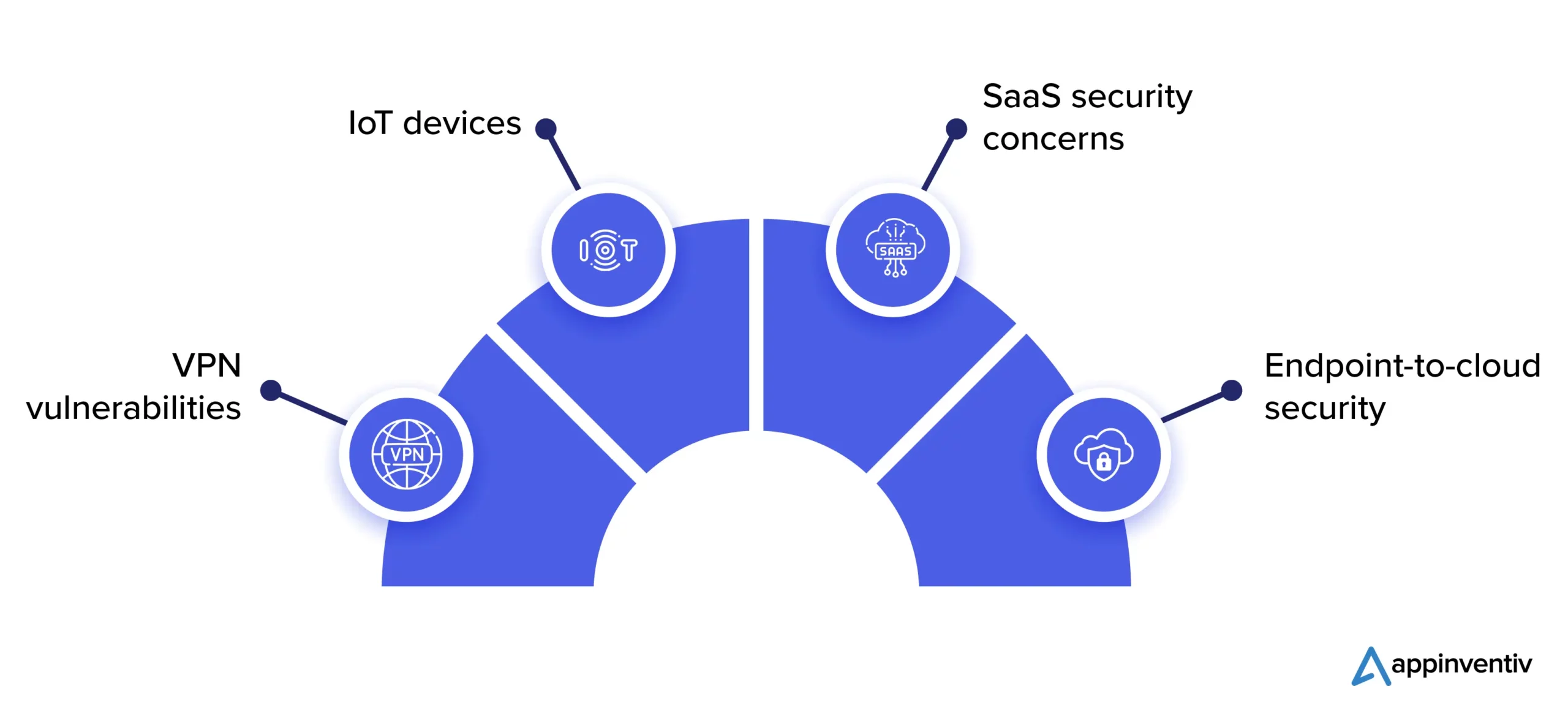
We cannot possibly discuss how to secure your cloud application without first discussing the types of security threats you can anticipate in 2023. Here is a brief list of the top cybersecurity risks.
Moving beyond VPNs
Virtual Private Networks (VPNs) have been a well-liked approach for organizations involving remote workers to safeguard their data, but they are inadequate to defend against emerging risks. Organizations should evolve beyond VPNs and establish more robust safeguards in place because they can be slow, unreliable, and prone to security breaches.
Network-connected devices
Since the advent of the Internet of Things (IoT), hackers have found a new avenue to target networks. By exploiting vulnerabilities in these connected devices, cybercriminals gain access to a network and move laterally within the network. Organizations must ensure that the devices are running on the latest software while installing necessary security patches. However, as explained in one of our articles, there are numerous benefits from the merger of cloud computing and IoT.
SaaS security concerns
With a massive increase in SaaS applications, hackers are finding new entry points into networks by accessing the vulnerabilities in such SaaS applications. Having robust cloud application security architecture can ensure that cloud-native application security is maintained at the highest level.
Endpoint-to-cloud security
In the entire spectrum that data travels, from the endpoint to the cloud, security protocols must address each of these layers and touchpoints because leaving even one of them exposed will dramatically increase the likelihood of a cyber threat.
To get a comprehensive picture of the top cloud security risks in 2023, read our article on the subject.
The benefits of a comprehensive cloud application security solution
Containing intellectual property, proprietary data, and business-critical infrastructure, securing cloud storage often plays a vital role in the success of an organization. Harnessing this data from the cloud is often the primary objective of targeted attacks. Therefore, the cloud in digital transformation offers dedicated and comprehensive benefits. Some of these benefits are:
The obvious protection from cyber attacks
Unmistakably, the most significant benefit of implementing cloud-based managed cyber security services is protection from cyber-attacks and data breaches. Such solutions embedded in the IT infrastructure enable organizations to detect and prevent potential attacks.
Compliance with Data Protection Regulations
Another benefit of emphasizing cloud app security measures is the ability to meet the compliance requirements of a regulatory body such as the EU’s GDPR and the California Consumer Privacy Act (CCPA). Focussing on cloud-based application security enables organizations to comply with these regulations, ensuring that data is stored and processed securely, reducing the likelihood of theft or unauthorized access. Cloud application security solutions help organizations meet these regulations by ensuring that sensitive data is stored and processed securely, protecting it from unauthorized access and theft.
Improved app performance and scalability
Adopting and implementing cloud security solutions also improve the app’s performance by eliminating potential vulnerabilities and backdoors in the code, making the app more robust, responsive, and scalable during spikes. This directly results in better productivity, customer satisfaction, and reduced downtime.
Better Visibility and Control
Securing cloud applications gives businesses better control and visibility of their cloud-based assets. Such systems give real-time information on unusual activity, login attempts, etc. This gives organizations a chance to defend their cloud-based assets before becoming victims of a cyber attack.
Cost saving
The age-old adage ‘prevention is better than cure’ somehow applies to securing cloud-based applications as well. Preventing cyber attacks is always a way through which companies can massively reduce unnecessary costs of responding to incidents. The aftermath of a cyber attack is even more drastic for the bottom line of any business. Therefore, ensuring application security in cloud computing is a definitive way to prevent revenue loss.
Improved collaboration and data sharing
One challenge enterprises often face is the inability to share data with various departments within the organization because of a lack of trust. Having robust measures for application security in cloud computing enables organizations to confidently share data that would remain siloed otherwise. This enhances collaboration between various departments and results in better productivity and outcomes for the end users.
Essential components and best practices for a robust cloud application security solution
Starting from advanced encryption of various states such as data-at-rest and data-in-transit and during storage to having robust firewalls are all essential components of a strong cloud application security solution. Encryption ensures that data, even if breached, will not be readable by anyone outside the organization, thus limiting the damage such incidents can cause. Firewalls, on the other hand, protect against network-based attacks.
[Also Read: How to Automate your Enterprise Cybersecurity with AI powered SOC]
Furthermore, organizations should have advanced access control and identity management systems to prevent unauthorized data access. In fact, a study by MIT Lincoln Laboratory provides a fresh take on identity management where they found that adopting ‘zero-trust security principles’ can limit the cybersecurity challenges posed by a malicious outsider or insider gaining access to the system.
MIT explains that the zero-trust policy treats “every component, service, and user of a system as continuously exposed to and potentially compromised by a malicious actor.” Therefore, a user has to prove his/her identity each time they request access. And all of those requests can be logged, traced, and analyzed to make the system more robust.
Measures such as multi-factor authentication, regular audits, disaster recovery, business continuity planning, and continuous monitoring are some of the other cloud application security best practices that every CSO and CISO should consider implementing in their organizations.
Also read: How can enterprises protect their data in cloud environments?
The importance of DevSecOps in mobile app security in the Cloud
DevOps has been hailed as a cornerstone of cloud app development. However, there are instances where this approach has given rise to security challenges. Therefore, developers and product managers are now integrating security as an integral part of the development process giving rise to DevSecOps. Along with continuous development and integration, DevSecOps implements continuous testing and monitoring of applications, because of which vulnerabilities become visible before they can be exploited.
Automated security tools and processes can also be built with the DevSecOps for cloud security, such as security scanning and testing, tipping off the engineering of any potential risk. DevSecOps further increases collaboration between the development and the security team, ensuring that security becomes a key part of the development process.
Compliances and standards of cloud application security
There are specific industry standards and regulatory compliances when it comes to the privacy of the consumer and the storage of data.
One of the most widely recognized standards is ISO 27001, which is used because it provides a detailed framework for information security management. The standard covers all aspects of security, including data on the cloud. Another required standard is SOC 2, which talks explicitly about cloud service providers and focuses on the security, availability, and privacy of the data stored on the cloud.
Apart from the standards, there are specific regulations that organizations must comply with. GDPR, for instance, “lays down rules relating to the protection of natural persons with regard to the processing of personal data and rules relating to the free movement of personal data.” Complying with GDPR ensures that your security standards are robust and customers can entrust their data with your business. Similarly, PCI DSS is the compliance requirement for credit card industry stakeholders.
How can Appinventiv make your cloud application secure?
Having almost a decade of experience in cloud managed services, we are well-versed in various nuances of managing cloud security.. From engineering site reliability to having delivered more than 200 cloud-based apps, we are always on our toes to ensure the security of our client’s applications or data in the cloud.
Having a plethora of cloud security managed services, we are the right partners for any entrepreneur or enterprise looking to secure their cloud application and/or data. Connect with our experts and take the first step towards making your cloud infrastructure immune to cyber threats.
Frequently Asked Questions Aout Cloud Application Security
What is cloud app security and why is it important?
Cloud app security is an umbrella term referring to the tools, technologies, and business POV of limiting and thwarting cyber threats. It is important because if a company’s data gets hacked, the organization may suffer huge losses in terms of goodwill and money.
How can cloud app security be improved?
Cloud security can be improved by having an action plan, proceeding with site reliability engineering, moving data to edge cloud etc.
How can businesses ensure that their cloud apps comply with data protection regulations?
Data protection regulations are a necessary gateway that organizations must pass through to handle customers or any other data carefully. A company can become compliant by having robust security measures, contingency plans, DDoS protection, etc.



Cloud Manufacturing Software - Benefits, Types, Development Process and Cost Analysis
Cloud computing is set to become a bigger part of the manufacturing industry's future as it continues to embrace digital transformation. With advancements in manufacturing software, cloud-based solutions are here to stay and only grow with time. The potential of ERP can be realized with the help of cloud manufacturing software, which eliminates the need…

Cloud Computing in Oil and Gas Industry - Identifying Business Opportunities and Challenges
In an industry where the pressure of data is as intense as the pressure in the deep sea, oil and gas companies grapple with managing enormous volumes of information, streamlining operations, and controlling costs. Traditional systems often buckle under the weight of this data deluge, leading to fragmented processes, operational inefficiencies, and hefty capital expenditures…