With 2.9 million apps in Google play store, there’s no denying the fact that the Android market is growing expeditiously. It has leveraged us with countless facilities and opportunities. But on the other side, it has alarmed us about the data threat. Since the Google play store does not strictly monitor the applications, as seen in the case of the iPhone app store, there are higher chances of approval of a malicious Android app.
“According to a survey, nearly 15-30 free, popular Android mobile apps secretly sent the sensitive information of users (contact numbers, voice mails, pictures, etc.) to remote servers. While, about two-thirds of the apps handled data in an enigmatic manner.”
As people use applications for performing almost every task, including banking, shopping, and booking, it is developer’s responsibility to look into the security matter. And thereafter, provide a convenient and secure user experience.
The mobile app developers enforce many advanced data protection mechanisms these days. However, not all remember about safeguarding less obvious elements that take part in data processing. If you are one among them, go through the following points to understand the concept of unintended data leakage and avoid data leaks.
What is a Data Leak?
The term can be utilized to describe information that is moved electronically or physically. Data leakage threats normally happen through the web and email, however it can likewise occur by data storage devices, for example, optical media, USB keys, and PCs and laptops.
A data leak is an unauthorized transmission of sensitive data which is accidentally exposed on the Internet or to an external destination with any other form including lost hard drives or laptops.
A data leak doesn’t need a cyber attack as it usually occurs from bad data security practices or accidental activity or inaction by an individual.
Data Leakage is also known as low and slow data theft. It has become a big issue for android data security, and the harm caused to any organization, inspite of its size or industry, can be serious and loss making. From declining income to a tainted reputation or enormous financial penalties to devastating lawsuits, this is a danger that any association will need to shield themselves from.
There’s no denying the fact that with the increasing adoption of mobile apps, malicious hackers have also improved the ways to hack mobile apps and steal user sensitive information. Meaning, both Android and iOS mobile apps are involved with popular data breach cases – be it Facebook Cambridge Analytica or the Dashdoor data breach case.
Below are the list of ways that will provide answers on how to avoid data leakage.
Let’s begin!
Ways to Prevent Data Leaks in an Android App

1. Use encryption keys
Data processing is a crucial sensitive part of the application development life cycle. It enables availability and faster processing of data. But since it contains sensitive information, it demands the need to be secured. According to the mobile app developers from various regions like android app developers in texas, a compromise with the security in data processing is the most common source of potential android data leaks. Wondering how? Well, as you might be familiar, sensitive data should be encrypted. But to encrypt any data and use it further, you need encryption keys provided by the app.
Many times, the keys are saved on the device, which is one of the reasons behind leakage of data. Actually, the encryption keys are saved in plain text form. If the hackers get access to such an encrypted database, they can easily find the public key and decrypt the database. Surprisingly, this is so easy that one can do it using public keys available online. This is a question about the concept of encryption and secure user experience.

To make it certain that the encryption keys are handled safely, the android application development company should use a set of Android data encryption tools called KeyStore. It is a class designed for storing and managing encryption keys with the most secure algorithms used across the globe.
“This tool of Android security tools not just protect the password, but other sensitive data as well.”
According to our experts, it handles everything in such a way that it is difficult for the hackers or unauthorized/spam software to get the information. On top of it, it provides the best performance and upgrade the data processing speed, provided all the encryption keys are handled wisely.
2. Implement HTTPs
Usually, HTTP protocol is used for transmission of data between a mobile app and a server. The data transferred using this protocol is not encrypted. So, it is better to use its encrypted version, i.e., HTTPs. Based on TLS/ SSL asymmetric cryptography, HTTPs renders a fairly higher level of security. However, it is necessary to be implemented with accurate care.
To encrypt communication via HTTPs, the server needs to have the facility to handle HTTPs connection. When this condition is applied, the client is supposed to send a request to the address beginning with ‘https’ protocol. During this, the server and client build parameters of the encryption in a process, namely handshake. On performing handshaking correctly, the communication is encrypted.
As per our experts, it is essential to fully implement the HTTPs connection. This is because someone might misuse the content in case of a man-in-the-middle attack. In this attack, a node (program or device) is kept in between the android app and the server which decrypts the connection just like the app, read it and re-encrypts it again. Neither the server and app, nor the user come to know about this mishap, and the sensitive data will get misused.
To prevent this situation, a developer can add a certificate inside the application code such that the app can verify the server certificate. This way, the Android mobile application will receive a response only from a server with a certain certificate.
“As per the top android app development services, the certificate pinning technique is not only a party of Android security mechanisms but should be employed on each client app responsible for encrypted communication using HTTPs connection. Without this, one can easily break the data encryption.”
3. Prevent data caching
Have you ever come across the situation when you have accidentally pasted the password into the login section, or sent it in a private message? Such things are common to observe, thanks to data caching.
Data Caching mechanism is to make the user’s life easier. The two common types of this mechanism are User’s dictionaries and Clipboard. The User’s dictionary suggests words on the basis of the user’s earlier word choice, while the Clipboard allows transferring data between mobile apps by saving it in the system memory temporarily.
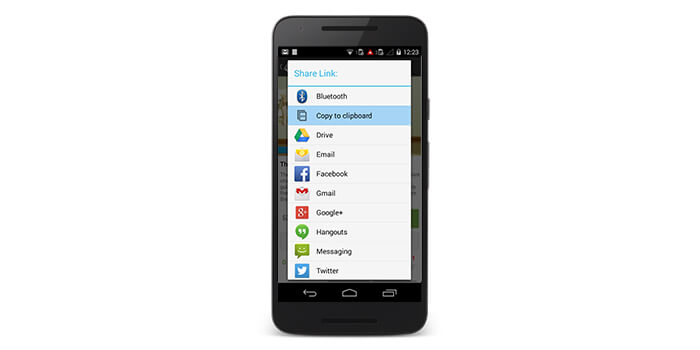
These elements make the user’s experience comfortable and efficient. That’s why various developers from different areas like android app developers in Texas include them in their Android app development strategy, regardless of the fact that it involves risk. As this procedure works automatically, it saves all the information without categorizing the content. Thus, passwords and other sensitive information are also saved as text in the clipboard and dictionary. Now, if the android device user goes to some app where the keyboard stimulates to replace the typed content with the password and he clicks okay, the password will be shared across the Internet as a searched phrase (search logs, search result or caching algorithm). Thus, the data security is compromised.
The best way to prevent this situation, as per the best android app development companies, is to set the appropriate input types (like ‘password’ types). And this way, block auto-caching as well as refrain copying the content to the clipboard.
4. Consider application logs
Other essential elements to consider in developing an Android mobile application is Logs. The Application logs are useful for the app professionals while analyzing the work of algorithms behind the data processing inside the applications. They can ensure that the sequence of processing is right or the results are desirable. But, unfortunately, the logs might contain sensitive information like passwords or access tokens and are stored locally on devices. They are publicly readable and accessible by many other apps installed on the same device if it works on an OS version lower than Android 4.2. The best method to deal with this situation is to ensure that your Android app does not use logs. Though they are helpful, the developers do not need them for the production version of the app.
5. Latest android development guidelines
Currently Google has begun carrying out strict rules and guidelines to make sure that any application that goes live on the Play Store is spam free. Thus, remaining up-to-date with the recent information and applying them into your application development process is again a helpful strategy for prevention of data leakage in an android app.
You can likewise prevent information leakage in your Android application by investing intensely in quality affirmation and guaranteeing that your application is updated time to time.
6. System components
All information and business logic depends on system components included in the Android SDK. It’s not clear for everybody that these components require extra protection. Unique security needs, specifically, these components of applications, which constitute the purported IPC (Inter-Process Communication) endpoints. This implies that those endpoints are used for sending and receiving information between different processes: of a similar application, different applications or system components. The most well-known approach to deal with such communication is to send data as broadcasts.
Wrapping Up!
Use of mobile applications for several purposes is on a steady rise in the modern cutting edge world. Individuals have begun utilizing mobile applications in a number of ways. Apps are being created to perform any assignment like buying, booking, work purpose, and banking. These and different other functions that include sensitive data should be shielded from unwanted mobile data leakage or data loss. It is the obligation of the android app development company to look into these security-related issues and give a protected and advantageous environment.
When talking about Data leakage and Security in an Android app, it is not limited to the above described points. There can be more places of data leakage and so, if you are building a mobile application, you need to be familiar with all the possible problems and should be eager to implement all the possible means of data protection and minimize the risk of android leaks.
If you are looking to develop an app that would be up to date with all the latest technologies of the current time and are secure, you can partner with our android application development services in USA, to help you expand your app journey.



The Mobile App Security Best Practices To Ensure a Hack-Proof App
Building a revolutionary mobile application is only the first step in mobile app development. Once you’ve built an app, there are thousands of mandatory processes that follow app development. One of those many crucial steps in mobile app security. In this article, we will explore what are the essential mobile app security practices that you…









